A friend of mine recently told me, “I tried three different apps just to find a doctor near me—...
Read More Service
- Managed IT Services The most resource-heavy task starts when you finish building IT infrastructure. Staff busy in managi...
- Cloud Managed Services Build and maintain an infrastructure strong enough to support new technologies. Set out a cloud to s...
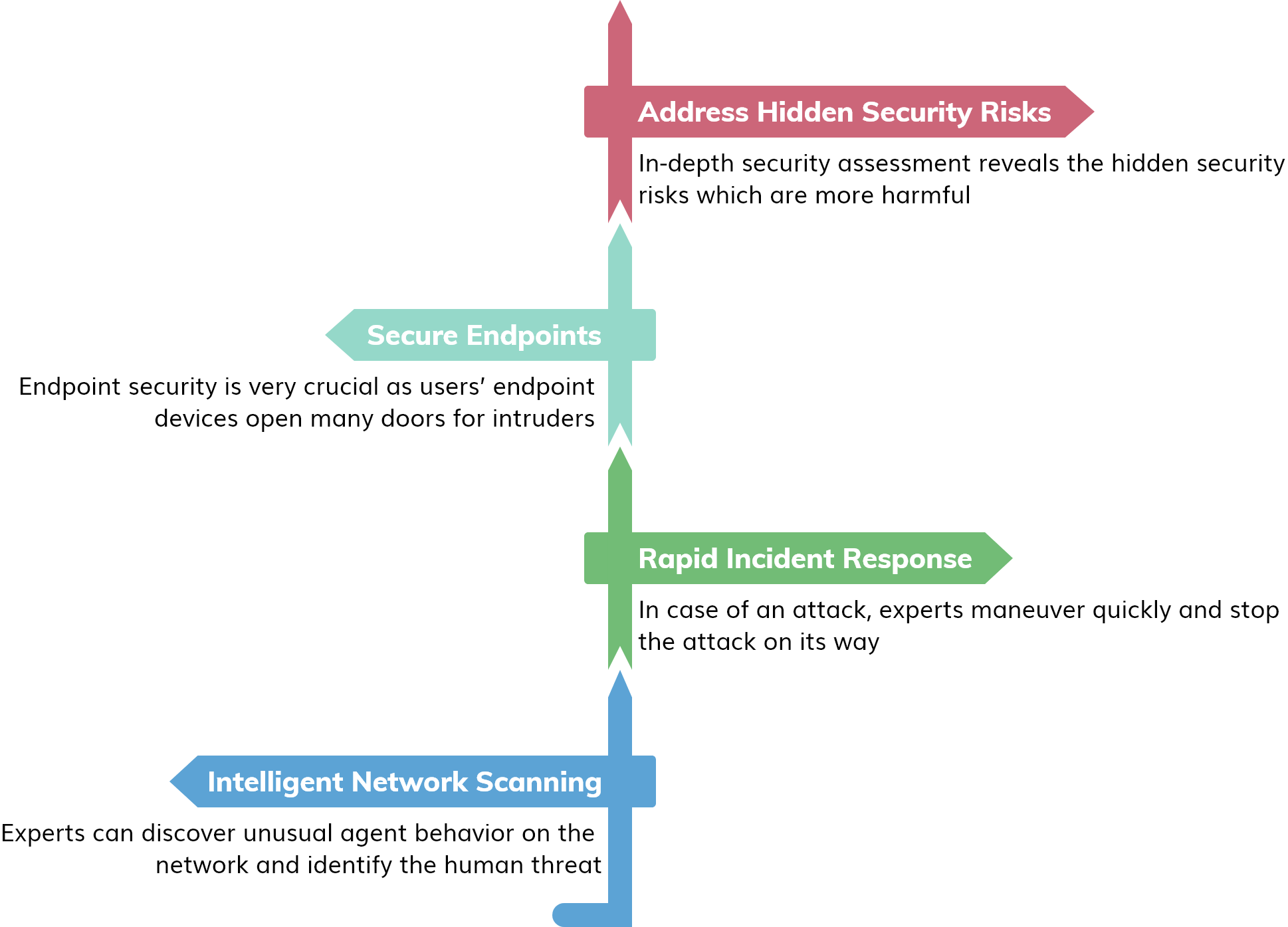
- Managed Security Services Avoid creating a paradise for intruders. Let our dedicated security specialists discover loopholes w...
- VoIP and Collaboration Do not let loosely-coupled and old-fashioned communication methods influence productivity. Talk to y...
- Healthcare Technology Test the market with MVP or launch the app with full force. We develop HIPAA/PHIPA-compliant apps ar...
- Robotic Process Automation Being a transparent RPA service provider in Ontario, Canada, we never intend to hide significant yet...
- Insights Category
- App Development
- Cloud
- Consulting
- Culture
- Cybersecurity
- FoIP
- Networking
- Uncategorized
- VoIP
Solutions
- Healthcare App Tech that treats your workflow right. From compliance to care coordination, we make healthcare IT easy—advice, setup, support, all in one smooth shot.
- Long-Term Care Pharm... Looking to simplify pharmacy operations? With over 30 years of healthcare tech expertise, we offer solutions like TELUS Health Kroll, cloud-based fax, online pharmacies, and RPA automation to boost efficiency and reduce costs.
- Retirement Home Streamline operations and enhance care with smart IT solutions. From telehealth to eMAR, we bring efficiency, reduce paperwork, and improve service quality for retirement homes.
- Long-Term Care Home ... The pandemic highlighted the need for better tech in LTC homes. We simplify the implementation, utilization, and maintenance of technology, helping you focus on care while we handle the IT.
- Real Estate Transform the way you sell and manage properties. With our real estate IT solutions, create immersive virtual property tours and streamline operations—all in one place.
- Manufacturing Optimize your manufacturing operations with custom AR solutions. From reducing troubleshooting costs to enhancing training and support, we provide end-to-end solutions to boost productivity and efficiency.
- Telemedicine App Dev... Get a telemedicine app that’s ready to go! We customize it to fit your unique needs, saving you time and money while you deliver top-notch care.